Cyber-espionage Operation: Shady RAT Brought to Light
Security company McAfee uncovers massive security breach
By: Chet Chung, Staff Writer
On Wednesday, August 3, computer security company McAfee, Inc., published a 14-page report detailing the largest hacking operation unearthed thus far. Dubbed “Operation Shady RAT” (RAT is an acronym for Remote-Access Tool, a program that allows users to access distant networks) by Dmitri Alperovitch, McAfee’s vice president of threat research, and author of the report, this barrage of attacks involves over 70 international organizations, including two Canadian government agencies. Security companys like McCafee and Trend Micro are constantly trying to stay one step ahead of computer hackers with innovative server and information security.
“With the goal of raising the level of public awareness today we are publishing the most comprehensive analysis ever revealed of victim profiles from a five year targeted operation by one specific actor,” writes Alperovitch in his report.
McAfee has uncovered evidence that suggests the operation began as early as July 2006, although the firm states that the attacks may well have begun prior to that date. With access to the logs of a Command & Control server used by the unidentified hackers, McAfee was able to identify 72 targets of security breaches. Many more compromised parties were found on the server’s logs but could not be identified due to a lack of accurate information. Of the many victims, more than half are U.S.-based, and 22 are government institutions of various countries. A total of 14 countries or states were targeted by Shady RAT.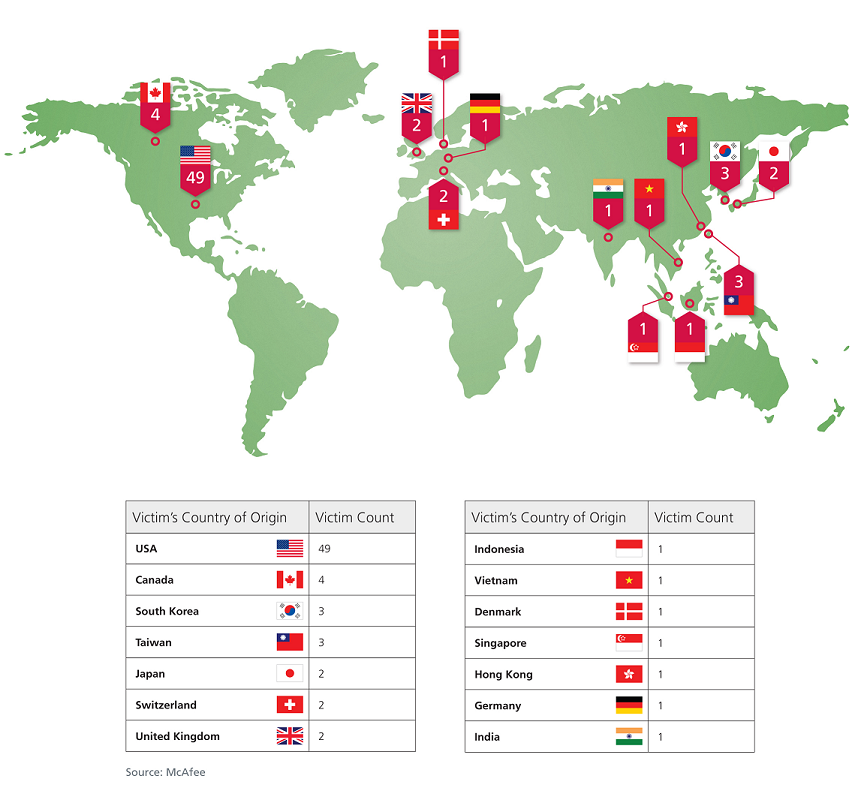
“This is further evidence that we need a strong cyber-defense system in this country, and that we need to start applying pressure to other countries to make sure they do more to stop cyber hacking emanating from their borders,” wrote Senator Dianne Feinstein (D-CA) in an e-mail to Vanity Fair.
Evidence of Operation Shady RAT was first uncovered in 2009, when a McAfee client – a US military contractor – detected questionable programs on its network. An investigation of the network showed that the military contractor had been infiltrated by a then unknown malware, classified as a Remote-Access Tool or RAT. This RAT allowed the hackers access to the military contractor’s network and therefore any valuable information stored on the network. Eventually, Alperovitch located one of the Command & Control servers used by the intruders to operate the RAT and immediately blocked McAfee clients from communicating with that server.
Though McAfee has proposed that a single “state actor” is responsible for the operation, the firm has declined to make any accusations due to company policy. However, many experts in the field of cyber-espionage and security have already arrived at a general conclusion given the circumstances of the hacking campaign.
“All signs point to China,” said James A. Lewis, director and senior fellow of the Technology and Public Policy Program at the Center for Strategic and International Studies, to Vanity Fair. Indeed, the location and activity of the operation’s attacks very much imply that China played an important hand in Shady RAT. Although nearly every country in Southeast Asia was marked by a cyber-attack, China went untouched. Moreover, the targets of the operation correspond considerably to China’s interests.
“Who else spies on Taiwan?” Lewis continued. “This isn’t the first we’ve seen. This has been going on from China since at least 1998.”
Alperovitch points out that those involved in Shady RAT were mostly after state secrets and sensitive information, contrary to the typical financial ambitions of hacking.
“We’re facing a massive transfer of wealth in the form of intellectual property that is unprecedented in history,” said Alperovitch to The Washington Post.
In his report, he contends that the compromised data and information of a given company could be used by competitors to build better products and, therefore, transpire into economic peril for companies, industries, and even whole countries. Individuals’ jobs as well as national security could be at stake. Nonetheless, as he notes, “what is happening to all this data—by now reaching petabytes as a whole—is still largely an open question.”
ARB Team
Arbitrage Magazine
Business News with BITE.
Liked this post? Why not buy the ARB team a beer? Just click an ad or donate below (thank you!)
Liked this article? Hated it? Comment below and share your opinions with other ARB readers!




























Share the post "Cyber-espionage Operation: Shady RAT Brought to Light"